Penetration Test Services
Penetration testing, which helps to identify and solve the logic and vulnerabilities in information systems, offers solutions that companies of all sizes can choose and secure their data. Our systems, which prevent malicious use of vulnerabilities in information systems, not only detect vulnerabilities, but also allow you to authorize access to systems. We identify the vulnerabilities in information systems one by one with my completely legal security tests and present them to you as a report. Then, we forward the authorization access to you and ensure that the system vulnerabilities are closed.
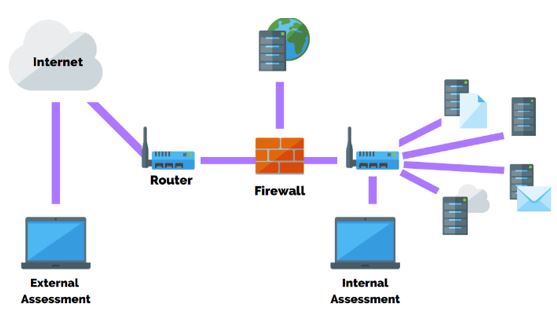
Penetration Test Services:
A penetration Test is a simulated attack to exploit weaknesses and vulnerabilities on a system, network, application, website, wireless network, or employees.
Knowing about vulnerabilities is just one step toward a secure enterprise. Penetration testing is conducted to validate not only the vulnerabilities already identified but to evaluate the implementation of security controls and tools.
As sophisticated as security devices are today, almost 90% of Cyber Attacks are caused by human error or behavior.
Security wrong configuration can happen at any level of an application stack, and these are the targets of modern hackers. The only way to know that your security tools are working is to test them.
It’s considered security best practice for business to perform penetration tests at least 1-2 times per year, however, compliance requirements or major infrastructure changes may require more frequent tests.
Benefits of Penetration Test
There are 5 main benefits to performing a penetration test including:
- Determining weakness in the hardware, software, or human assets of an organization in order to develop controls.
- Maintaining the 3 triads of cyber security – Confidentiality, Integrity, and Availability.
- Ensuring that controls which have been implemented are adequate.
- Providing intelligence and insight of an organization’s security measures by understanding how it could be and likely will be attacked and what steps should be taken to secure the organization.
- Improving the overall security posture of an organization.